Every day in the world of Decentralized Finance can be a struggle between maintaining full custody over your crypto assets and losing all your assets to one of many possible schemes, scams, or hacks.
It can be terrifying knowing that you could wake up to find your wallet completely drained of its assets. However, it doesn’t have to be that way.
There are some measures you can take to protect yourself from 90% of the scams & hacks out there and in this article, we will go over four of these measures.
So, let’s dive in!
Using the Right Security Tools
Crypto scams and their techniques are becoming more sophisticated by the day, making them even more difficult to spot until it’s too late.
Most common among such scams is Phishing: A technique that deceives a victim into revealing sensitive information such as the seed phrase or private keys to a wallet containing assets.

This is usually done by cloning a link or an entire website to look nearly identical to a legitimate and popular DeFi platform such as Uniswap. The unsuspecting victim connects their wallet to this fake website and all assets including Crypto, NFTs, etc. are immediately drained.
A solid protection against this is the use of crypto tools like Wallet Guard.

Wallet Guard is a simple browser extension that interfaces with any crypto-based platform before your wallet gets connected to it. It reveals hidden details about the website that can determine if the platform is fraudulent or not and presents a warning in plain language to the user before any further actions are taken.
It is especially useful against phishing links and websites that are aimed at scamming victims without their knowledge. A must-have for every crypto user.
Watch Out for Strange DMs and Emails from Scammers
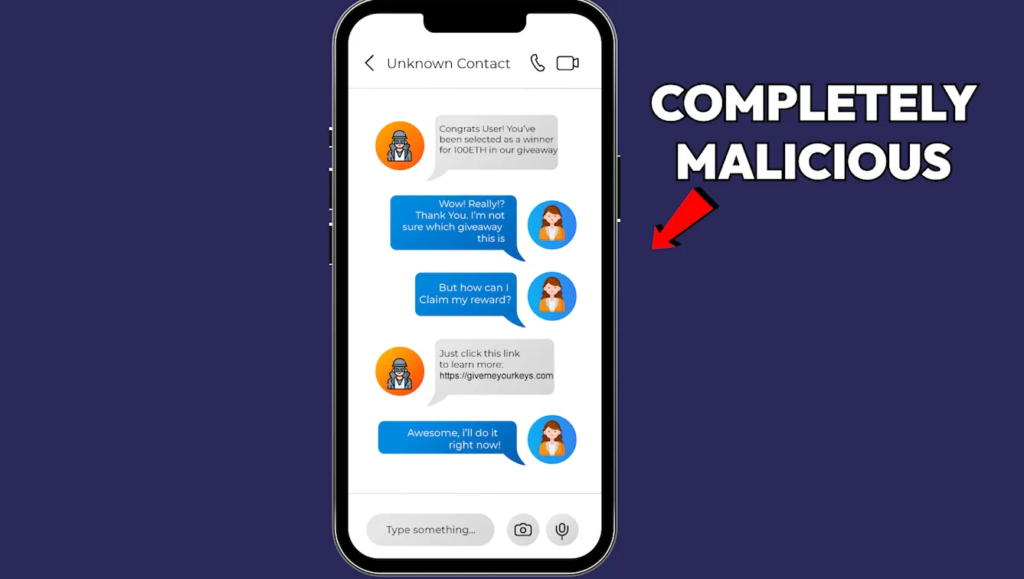
This is one of the oldest tricks in the scamming book, but it still thrives today because of the number of victims who keep falling for it.
The technique involves social engineering where a potential victim receives a DM or an email from a well-known crypto project, exchange, or KOL. The message would usually contain subjects such as:
-Winning a Giveaway or Promo
-Qualifying for an Airdrop
-Some sort of partnership with other KOLs
-A compromise on an account that needs immediate attention
-Zoom meeting with a Crypto Project etc.
The victim is then prompted to click a link which instantly downloads malware into the computer and the malware collates data from crypto wallets that contain private keys, passwords, or seed phrases and sends it to the scammer after which the content of the wallet is immediately drained.
Such messages, while not always malicious will always have a higher chance of being so and should be avoided especially if there was no premise to such messages. If you didn’t consciously enter into any campaigns that offer a potential reward, then you shouldn’t expect any messages about a reward in the first place.
You can also keep an eye out for clues in the messages such as spelling errors or carefully chosen words like ‘URGENT’, ‘Don’t miss out’, and ‘Click this Link right now’ which are aimed at making victims click malicious links impulsively without thinking twice. Those are some dead giveaway clues you can use to protect yourself from fraudulent emails and DMs.
Always Triple-Check Wallet Addresses
New scams in crypto are born much faster than we can imagine. One particular tactic has been gaining a lot of traction is Address poisoning.
This crypto scam targets crypto users who are accustomed to copying and pasting wallet addresses directly from their transaction history to make a transaction and aims to trick the user into sending funds to the wrong address.
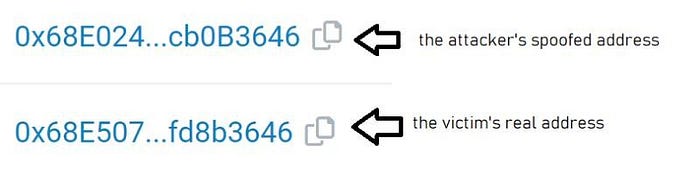
Here is how it works:
- The scammer sends a very small amount of cryptocurrency to the victim’s wallet causing the scammer’s address to be recorded in the victim’s wallet history.
- The scammer then creates an address that is identical to a legitimate address from the victim’s previous transactions making it difficult for the victim to spot the difference.
- When the victim later intends to send cryptocurrency, they typically go to their history to copy the wallet address and by not being able to notice the fake address, the victim is more likely to copy the scammer’s address instead of the intended recipient’s address, sending funds to them which cannot be retrieved.
The scam only works on users that revisit their wallet history to copy addresses and as such, the solution to this is simple:
1. Avoid Copying Addresses from Your Transaction History
2. Only Copy Addresses from Trusted Sources
Use a Hardware Wallet
All the scams we talked about so far and even most crypto scams in general are only applicable to users whose wallets are directly installed on their computers.
But with Hardware wallets like Ledger or Trezor, the safety of your assets is greatly improved. These wallets do not leave any footprints on your computer and give no room for attackers to get access to your crypto asset.

These physical devices are designed to keep your crypto assets offline and only accessible by the owner at all times. Sure, they cost quite a bit to purchase but they also save you a lot of potential trouble in the long run.
So, if you own large sums of crypto that you cannot afford to lose, a hardware wallet is definitely worth the investment.
Conclusion
While this list is not exhaustive, it contains useful knowledge that could potentially save you from being scammed or hacked. But regardless, the responsibility will always remain in the hands of the user to protect themselves from being scammed.
Interacting with DeFi platforms will require an extra sense of caution and reluctance to click buttons quickly. It’s the price to pay for self-custody of assets.






Pingback: A Guide to Popular Cryptocurrencies - Dexifier Blog
Pingback: How to Set Up Your Cryptocurrency Wallet